The Growing Threat Landscape of Connected Vehicles
The Evolving Nature of Cyber Threats
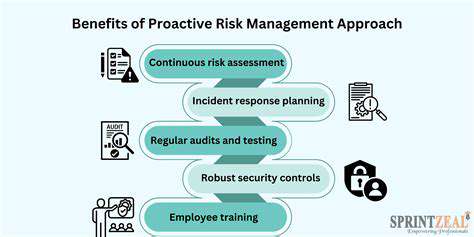
The digital landscape is constantly evolving, and with it, the tactics and techniques employed by cybercriminals. Traditional methods of attack are constantly being refined and new, more sophisticated methods are emerging. This ongoing evolution makes it increasingly challenging for organizations to stay ahead of the curve and protect their valuable data and systems. Understanding the evolving nature of these threats is crucial for proactively mitigating risks.
From ransomware attacks that cripple entire operations to data breaches that compromise sensitive information, the spectrum of cyber threats is vast and constantly shifting. This necessitates a proactive and adaptive approach to cybersecurity, one that goes beyond reactive measures to anticipate and prevent emerging threats.
The Rise of Sophisticated Malware
The development of advanced persistent threats (APTs) presents a significant challenge. These sophisticated attacks often go undetected for extended periods, allowing attackers to steal sensitive data, disrupt operations, and even manipulate systems for malicious purposes. This makes early detection and proactive defense strategies critical for mitigating the damage caused by such threats.
Malware is becoming increasingly sophisticated, often employing techniques to evade traditional security measures. The use of polymorphic malware, which can change its code structure to avoid detection, is one example of this trend. This necessitates the use of advanced threat intelligence and adaptive security measures to counter these evolving threats.
The Impact of Social Engineering
Social engineering attacks, which exploit human psychology to gain access to systems or information, are becoming increasingly prevalent. These attacks often target employees through phishing emails, malicious websites, or other deceptive methods. The success of social engineering attacks highlights the importance of employee training and awareness programs in strengthening cybersecurity defenses.
The human element is often the weakest link in a security chain. Cybercriminals are adept at manipulating individuals through social engineering tactics. This necessitates comprehensive training for employees to recognize and avoid common social engineering traps, as well as fostering a culture of cybersecurity awareness.
The Growing Importance of Data Protection
Data breaches are a significant concern, with sensitive information often being targeted and exploited. Protecting data from unauthorized access and use is paramount for maintaining trust with customers and avoiding financial and reputational damage. Implementing robust data encryption and access control measures is essential for mitigating the risks associated with data breaches.
The increasing reliance on digital platforms for storing and processing sensitive data heightens the importance of data protection measures. Organizations must prioritize implementing strong encryption protocols and access controls to safeguard data and maintain compliance with relevant regulations.
The Role of IoT Devices in Expanding Threat Vectors
The proliferation of Internet of Things (IoT) devices introduces new vulnerabilities into networks. These devices, often with limited security features, can be exploited to gain access to critical systems and data. Securing these devices and ensuring adequate security protocols for IoT networks is vital for preventing widespread compromise.
The increasing interconnectedness of devices through IoT networks creates new attack surfaces. This necessitates a comprehensive approach to security that extends beyond traditional computer systems to include IoT devices. Developing robust security protocols and implementing secure communication channels are crucial for safeguarding against exploitation.
The Importance of Data Privacy and Security in Connected Cars
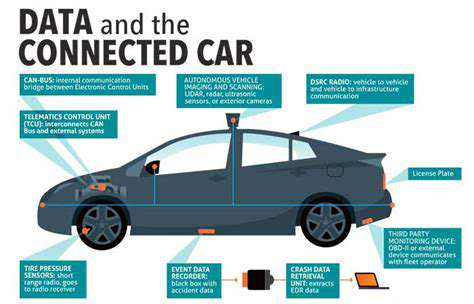
Protecting Personal Information in the Digital Age
In today's interconnected world, personal data is collected and utilized at an unprecedented rate. From online shopping to social media interactions, we constantly share information about ourselves, and the increasing reliance on digital platforms necessitates a heightened awareness of data privacy. Protecting this personal information is paramount, not just for individual well-being, but for the stability and security of society as a whole. Data breaches can have devastating consequences, impacting individuals financially, emotionally, and reputationally.
Understanding the potential risks associated with data breaches and the importance of safeguarding personal information is crucial. The consequences of inadequate data protection can range from minor inconveniences to major financial losses, identity theft, and emotional distress. This underscores the vital role of individuals and organizations in actively protecting sensitive data.
Understanding Data Privacy Regulations
Numerous regulations worldwide are designed to protect personal data, aiming to establish clear guidelines for data collection, use, and security. These regulations, such as GDPR in Europe and CCPA in California, are vital in establishing a framework for responsible data handling. These frameworks aim to empower individuals with control over their personal information and provide recourse in case of violations. Compliance with these regulations is crucial, not only to avoid penalties, but also to foster trust and transparency.
The Role of Technology in Data Protection
Technological advancements play a significant role in both the collection and protection of data. While sophisticated technologies can enable efficient data management, they also present new challenges regarding security and privacy. Implementing robust security measures, including encryption, access controls, and intrusion detection systems, is critical in mitigating risks. The integration of these technologies is essential for effective data protection.
Furthermore, data anonymization and pseudonymization techniques can help to reduce the risk of unauthorized access while still allowing for useful data analysis. These techniques are becoming increasingly important as data sets grow in size and complexity.
The Impact of Data Breaches
Data breaches can have devastating consequences for individuals and organizations. Financial losses, identity theft, reputational damage, and emotional distress are just a few of the potential outcomes. These breaches can also lead to legal and regulatory repercussions, impacting the trust and confidence in institutions. The financial burden of data breaches can be substantial, requiring significant investment in recovery and remediation efforts.
The Importance of Data Minimization
Collecting and storing only the necessary data is crucial for data privacy. Data minimization principles ensure that only the minimum amount of data required for specific purposes is collected and retained. This approach not only reduces the risk of breaches but also simplifies data management and ensures compliance with various regulations. Data minimization is essential for efficient data handling and safeguarding sensitive information. It promotes accountability and transparency, which in turn builds public trust.
Enhancing Data Security Culture
Establishing a strong data security culture within organizations is essential for comprehensive protection. This involves fostering awareness and training among employees regarding data privacy best practices, promoting a proactive approach to security, and implementing clear policies and procedures. Strong data security culture is a significant factor in preventing data breaches and mitigating risks. Regular security audits and incident response plans can further enhance security posture and ensure swift and effective responses to breaches.