The Evolving Threat Landscape for Autonomous Vehicles
The Rise of Sophisticated Cyberattacks
Today's digital environment faces an alarming escalation in highly targeted and complex cyber threats. While conventional malware remains widespread, attackers now integrate it into broader, more intricate campaigns. Malicious actors utilize techniques like psychological manipulation of users, software vulnerability exploitation, and previously unknown security flaws to infiltrate protected systems. This heightened complexity presents formidable obstacles for businesses across all sectors, compelling them to overhaul defensive approaches and prioritize advanced threat detection capabilities. The current security climate necessitates anticipatory actions to maintain protective advantages.
Modern intrusion attempts typically follow multi-phase operations, beginning with extensive surveillance to map target networks and identify weak points. This preparatory work enables precise customization of attack methods to specific security gaps. Subsequent infiltration often occurs through stolen access credentials or unpatched software vulnerabilities. The meticulous nature of these operations renders conventional security solutions increasingly ineffective, demanding implementation of comprehensive defense-in-depth strategies with multiple overlapping safeguards.
The Growing Importance of Proactive Security
Contemporary security challenges highlight the essential nature of preventive protection mechanisms. Dependence on traditional reactive tools like antivirus programs and network barriers proves inadequate against today's sophisticated threat actors. Enterprises must transition toward forward-looking security frameworks incorporating predictive threat analysis, systematic weakness evaluation, and comprehensive staff education programs. These integrated solutions provide holistic protection by identifying and neutralizing potential threats before exploitation occurs.
Human factors remain critical in security ecosystems. Comprehensive training programs significantly enhance workforce ability to recognize and resist deceptive communications, psychological manipulation attempts, and other prevalent attack methods. Since personnel often represent the most vulnerable security component, empowering them with detection skills and response protocols dramatically strengthens organizational defenses. Strategic investment in these preventive measures yields long-term security dividends.
Equally vital are well-developed incident management protocols. Clearly defined response procedures enable rapid containment and minimization of security events. This requires unambiguous role definitions, established communication channels, and readily available response resources. In our interconnected digital environment, proactive security measures form the foundation for safeguarding sensitive information assets.
Protecting the Vehicle-to-Vehicle (V2V) and Vehicle-to-Infrastructure (V2I) Communication Channels
Securing the V2V Communication Layer
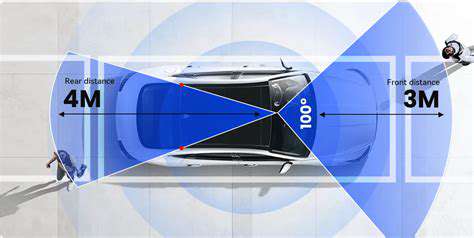
Guaranteeing secure data transmission between autonomous vehicles represents a critical safety requirement for V2V networks. This demands implementation of advanced encryption standards and identity verification processes to block unauthorized message interception or alteration. State-of-the-art cryptographic methods, integrated with protected key administration frameworks, prove essential for maintaining data accuracy and privacy during exchanges. This comprehensive security methodology effectively prevents hostile interference with vital vehicular communications, ensuring roadway safety.
Deployment of network monitoring solutions within V2V systems provides additional critical protection. These surveillance mechanisms continuously scan communication pathways for abnormal patterns and potential threats. Immediate detection and neutralization capabilities prove fundamental for timely threat response, thereby enhancing overall network security. Such preventive security measures become increasingly vital as vehicular communication technologies advance.
Protecting Against Jamming and Interference
V2V and V2I networks remain susceptible to intentional disruption attempts that could compromise essential information exchanges. Effective defensive strategies must incorporate interference detection technologies and alternative communication routes to preserve connectivity during attacks. Dynamic communication standards capable of automatic adjustment to signal interference ensure consistent operational reliability.
Network protocol development must account for various interference sources including competing radio signals and environmental conditions. Thorough understanding of these factors enables creation of resilient communication architectures capable of withstanding disruptive influences. Advanced signal analysis methods play a crucial role in countering interference and maintaining stable connections across diverse operating environments.
Securing the V2I Communication Interface
The infrastructure communication channel requires stringent protective measures to prevent unauthorized traffic signal manipulation or data corruption. Sophisticated verification processes must authenticate both vehicle and infrastructure components, establishing mutual trust and preventing system compromise by malicious entities.
Secure cryptographic key administration systems prove indispensable for protecting data integrity during vehicle-infrastructure exchanges. These frameworks must demonstrate exceptional resistance to compromise while incorporating secure key distribution and cancellation mechanisms, ensuring continuous protection of sensitive operational data.
Addressing Privacy Concerns in V2V/V2I
Data collection practices in vehicular networks generate substantial privacy considerations, particularly regarding potential information exposure or misuse. Implementation of rigorous data anonymization and encryption protocols becomes essential for personal privacy protection. Information collection should adhere to minimum necessary principles, with secure storage and processing protocols preventing unauthorized data access.
Clear data usage policies and explicit consent procedures help ensure user awareness regarding information collection and sharing practices. Regular security evaluations and vulnerability testing remain necessary to identify potential privacy risks and maintain compliance with relevant data protection standards.
Maintaining System Integrity and Availability
Ensuring continuous operation of vehicular communication networks represents a fundamental requirement for autonomous transportation safety. Redundant network architectures and data preservation systems help mitigate service interruptions from technical failures or attacks. Implementation of self-healing protocols and rapid recovery mechanisms proves equally critical.
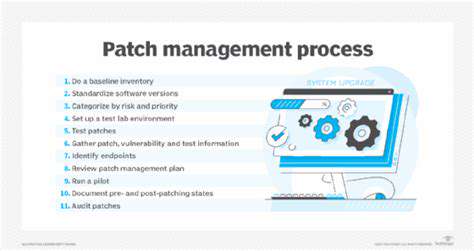
Ongoing system maintenance and updates remain vital for addressing emerging vulnerabilities and maintaining communication reliability. This includes continuous performance monitoring, vulnerability identification, and prompt deployment of security patches. Persistent surveillance and preventive maintenance ensure sustained system stability and operational integrity.