Targeting System Vulnerabilities
Digital systems often contain exploitable weaknesses that malicious actors actively seek to leverage. The process of identifying and correcting these security gaps before they're exploited remains a fundamental aspect of modern cybersecurity. Attackers frequently focus on the most accessible entry points, which can include outdated software, misconfigured settings, or human error. When these vulnerabilities are successfully exploited, the consequences can range from minor disruptions to catastrophic data breaches with significant financial implications.
Comprehensive vulnerability management requires continuous effort. Organizations that implement regular security assessments dramatically improve their defensive posture. These evaluations should encompass penetration testing, vulnerability scanning, and thorough system audits. Equally important is the deployment of strong authentication mechanisms and maintaining awareness of emerging threat patterns in the cybersecurity landscape.
Current Exploitation Techniques
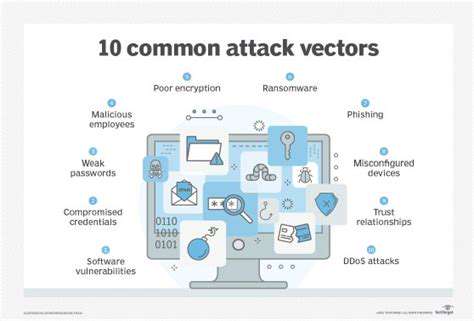
Cybercriminals employ diverse strategies to compromise systems, with social engineering remaining particularly effective. These psychological manipulations often take the form of sophisticated phishing campaigns that mimic legitimate communications to harvest credentials. Attackers frequently create convincing replicas of trusted websites to deceive users into entering sensitive information.
Malware distribution continues to evolve as a persistent threat vector. Modern malicious software includes advanced variants that can evade traditional detection methods. These programs might operate stealthily for extended periods while exfiltrating data or establishing backdoor access for attackers. The increasing complexity of these threats necessitates equally sophisticated defensive measures.
Application vulnerabilities present another significant concern. Poorly written code or inadequate input validation creates opportunities for injection attacks, which can lead to complete system compromise. Network infrastructure weaknesses, particularly in firewall configurations or outdated protocols, similarly provide avenues for unauthorized access.
Physical security lapses can be just as damaging as digital vulnerabilities. Unauthorized access to server rooms or workstations can bypass many digital security measures, emphasizing the need for comprehensive security strategies that address all potential attack surfaces.
Protecting Data and Critical Systems: Defense Strategies
Advanced Access Management
Modern access control systems form the foundation of effective security architectures. The principle of least privilege should govern all permission assignments, ensuring users only receive the minimum access necessary for their roles. Multi-factor authentication has become essential rather than optional, particularly for privileged accounts. Password policies must enforce complexity requirements while balancing usability considerations.
Continuous monitoring of access patterns can reveal potential security incidents before they escalate. Implementing role-based access controls allows for precise permission management that adapts to organizational changes. Regular audits of user privileges help maintain appropriate access levels as personnel roles evolve over time.
Cutting-Edge Threat Identification
Contemporary security operations require advanced detection capabilities. Modern intrusion prevention systems incorporate behavioral analysis to identify anomalous activity that might indicate compromise. These systems now integrate machine learning algorithms capable of detecting novel attack patterns that might evade signature-based detection methods.
Security information and event management platforms provide centralized visibility across diverse systems. When combined with up-to-date threat intelligence feeds, these solutions enable proactive defense against emerging global threats. The correlation of security events across multiple data sources significantly improves detection accuracy and response times.
Secure Development Practices
Application security must begin during the design phase and continue throughout the development lifecycle. Developers require training in secure coding principles and access to tools that identify vulnerabilities during the coding process. Regular security testing, including static and dynamic analysis, should precede any production deployment.
Timely application of security patches remains critical for maintaining system integrity. Organizations must establish efficient processes for evaluating and deploying updates while minimizing operational disruption. Creating a security-conscious development culture ensures that protective measures remain a priority throughout all technical initiatives.
Comprehensive Continuity Planning
Effective disaster recovery strategies address both technical restoration and business process continuity. These plans should detail procedures for data recovery, system restoration priorities, and alternative operational methods during disruptions. Regular testing through simulated incidents verifies plan effectiveness and identifies areas for improvement.
Business continuity planning must account for various disruption scenarios, including cyberattacks. Clear communication protocols and predefined decision-making authority help maintain operational stability during crises. Maintaining secure, geographically distributed backups ensures critical data remains available even during significant infrastructure failures.