The Growing Threat Landscape in the Modern Automotive Industry
The Evolving Nature of Cyberattacks
In today's digital age, the automotive industry faces an ever-changing array of cyber threats that grow more complex by the day. Malicious actors now utilize advanced methods to find and exploit system weaknesses. What were once rare security breaches have transformed into frequent, targeted assaults that jeopardize both infrastructure and confidential information. The prevalence of ransomware campaigns, deceptive phishing attempts, and manipulative social engineering schemes highlights the urgent need for comprehensive security protocols and ongoing staff education.
Conventional security solutions often fall short against these modern challenges. A defense-in-depth strategy is essential, combining various technological safeguards and proactive measures to create a resilient security framework. Beyond basic antivirus programs and firewalls, organizations should deploy advanced tools like intrusion prevention systems, comprehensive security monitoring platforms, and well-practiced incident response procedures.
The Rise of Ransomware
Ransomware incidents now pose a critical threat to businesses across all sectors, leading to severe financial consequences and operational paralysis. As cybercriminal organizations refine their techniques and focus on essential services, the potential damage multiplies. Developing rapid system recovery capabilities has become imperative to reduce downtime and financial impact following an attack. Maintaining isolated backup systems and detailed continuity plans forms the foundation of effective ransomware defense.
The Importance of Data Protection
Information security breaches represent one of the most damaging threats organizations face, with potential consequences including reputational harm and legal liabilities. Such incidents can trigger substantial monetary penalties, compliance violations, and costly litigation. Safeguarding confidential data requires implementing multiple protective layers, including strict permission settings, advanced encryption methods, and periodic security evaluations. These measures help control risk exposure while ensuring adherence to industry regulations.
The Impact of IoT Devices
The rapid adoption of Internet-connected devices has dramatically increased potential entry points for cyber intruders. Many of these smart devices ship with inadequate security protections, making them prime targets for network infiltration. Properly securing these endpoints and controlling their network access is fundamental to maintaining overall system integrity. Companies must establish specialized security procedures that account for the specific weaknesses inherent in IoT technology while ensuring continuous oversight and management.
The Role of Human Error
Mistakes by personnel continue to represent a major security vulnerability across industries. Whether through falling for fraudulent emails, succumbing to psychological manipulation tactics, or accidentally exposing sensitive data, human actions often create security gaps. Comprehensive security awareness initiatives and regular training sessions play a vital role in minimizing these risks. Effective programs should cover secure password practices, email verification techniques, and methods for identifying potential security threats.
The Growing Threat of Insider Threats
Internal security risks remain a persistent and frequently overlooked danger. Whether through deliberate malicious actions or careless behavior, employees and partners can inadvertently compromise organizational security. Establishing rigorous permission systems and comprehensive monitoring solutions is essential for identifying and neutralizing internal security threats. Conducting periodic security reviews and pre-employment screening helps identify and mitigate potential risks from within the organization.
The Need for Proactive Security Measures
Anticipatory security practices have become essential for maintaining protection against evolving digital threats. These include real-time surveillance activities, systematic vulnerability scanning, and controlled penetration testing exercises. By detecting and addressing security weaknesses before exploitation occurs, organizations can maintain superior defensive postures. This forward-looking strategy enables businesses to adapt to new threat patterns while preserving robust security standards.
Identifying and Mitigating Common Attack Vectors
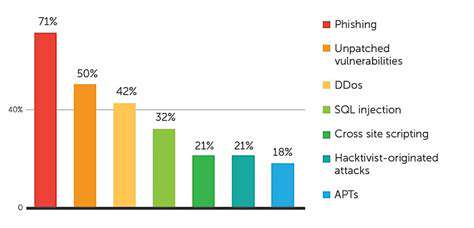
Identifying Common Challenges
Recognizing the exact obstacles that impede project success forms the foundation of effective risk management. A complete evaluation should examine all possible impediments, ranging from limited resources and ambiguous objectives to team conflicts and unforeseen technical complications. Pinpointing the fundamental causes behind these issues is paramount, as superficial solutions rarely provide lasting resolution. This detailed analysis enables preventive rather than corrective action, significantly improving the chances of successful outcomes.
Additionally, accurately categorizing the nature of these challenges proves equally important. Are the primary difficulties related to logistics, budgeting, or perhaps personnel dynamics? Distinct problem types demand specialized approaches. For instance, financial constraints might require exploring alternative funding streams, while team disputes could benefit from structured conflict resolution processes. Accurate problem classification leads to optimally tailored solutions.
Developing Effective Mitigation Strategies
After thorough problem identification, creating robust countermeasures becomes critical. This phase involves designing specific action plans to resolve each documented issue, complete with implementation timelines, designated responsibilities, and quantifiable success indicators. Well-structured strategies dramatically improve problem resolution effectiveness.
Key elements of comprehensive mitigation planning should incorporate backup procedures for unexpected developments, alternative approaches for potential obstacles, and systematic progress tracking mechanisms. These components help maintain project momentum while enabling prompt responses to any deviations. Maintaining open communication channels and fostering collaborative problem-solving among all participants is equally vital, creating an environment where challenges can be openly addressed.
Proactive risk analysis can help predict future complications, allowing organizations to implement protective measures before issues escalate into major problems affecting project schedules and costs. This preparatory work represents a fundamental aspect of effective project management. By anticipating possible risks, teams can develop contingency plans for various scenarios.
Implementing and Monitoring Mitigation Tactics
Executing developed mitigation strategies demands careful coordination and consistent oversight. Assigning dedicated personnel to supervise implementation ensures adherence to planned actions and schedules. Regular status updates and performance assessments help evaluate strategy effectiveness and identify required modifications. Maintaining detailed records of all actions and decisions provides valuable reference material for future improvements.
Ongoing evaluation proves critical for achieving desired results. Regular assessments comparing actual progress against planned mitigation efforts enable identification of emerging issues and necessary strategy adjustments. Fostering transparent communication and cooperative efforts among team members significantly enhances the likelihood of successful outcomes.
Strengthening Security Throughout the Vehicle Lifecycle
Understanding the Vehicle's Digital Architecture
Contemporary vehicles represent intricate networks of interconnected electronic components, control modules, and software systems. This sophisticated digital framework enables advanced features like autonomous driving assistance and multimedia systems while simultaneously creating potential security vulnerabilities. Comprehensive knowledge of system components, their interactions, and possible exploitation methods forms the basis for developing effective security solutions spanning the entire operational lifespan.
Securing the Design Phase
Security considerations should be incorporated during initial vehicle design stages. This involves applying secure development methodologies, implementing protected communication standards, and conducting exhaustive threat analysis to identify system weaknesses. Addressing potential security flaws during design helps prevent costly remediation efforts during later lifecycle phases.
Protecting the Manufacturing Process
Production facilities represent critical security control points. Implementing stringent physical security controls prevents unauthorized access to vehicle electronics during assembly and quality testing. Equally important are secure supply chain management practices that verify component origins and prevent introduction of compromised parts or malicious code. Rigorous supplier evaluation processes form an essential part of this protective strategy.
Implementing Secure Software Updates
Timely, protected software maintenance represents a crucial security practice for addressing vulnerabilities and enhancing system protections. Reliable update mechanisms must incorporate secure distribution channels, integrity verification processes, and recovery procedures for update failures. Careful implementation minimizes service interruptions while maintaining positive customer experiences.
Ensuring Cybersecurity During Operation
Continuous security monitoring remains essential throughout vehicle service life. Advanced threat detection systems can identify anomalous activities and generate security alerts. Secure remote diagnostic capabilities and wireless update functionalities enable ongoing security improvements without physical service requirements. These measures help maintain optimal security conditions during vehicle operation.
Addressing the Challenges of Data Privacy
The growing volume of vehicle-collected data, encompassing everything from driver behavior to environmental conditions, presents significant privacy considerations. Establishing secure data handling procedures, explicit user permission systems, and transparent privacy policies is essential. Compliance with data protection regulations helps maintain consumer trust while preventing unauthorized information access.
Promoting Collaboration and Standardization
Effective automotive cybersecurity requires cooperation among manufacturers, component suppliers, security researchers, and regulatory agencies. Developing uniform security standards and shared best practices ensures consistent protection throughout the industry. Knowledge exchange and open communication accelerate development of robust security solutions while keeping all parties informed about emerging threats.