The Criticality of Perception Systems in Autonomous Vehicles
Understanding the Fundamentals of Perception Systems
Modern autonomous systems rely heavily on perception technologies to interpret their surroundings. These complex frameworks, powered by advanced sensor arrays and algorithmic processing, form the backbone of situational awareness for machines. Mastering these foundational concepts proves indispensable for engineers developing next-generation intelligent systems. The interplay between hardware limitations and algorithmic biases creates unique challenges that require careful consideration during system design.
Environmental interpretation involves sophisticated data conversion processes. Visual, auditory, and spatial information each demand specialized handling techniques. System architects must account for these variations to ensure consistent performance across diverse operating conditions and unexpected scenarios.
The Role of Sensors in Data Acquisition
Sensor arrays serve as the primary interface between autonomous systems and their environments. Selection of appropriate sensing modalities directly determines system capabilities and operational boundaries. Various detector types specialize in capturing distinct environmental characteristics including electromagnetic radiation, pressure fluctuations, and thermal gradients. Strategic sensor selection remains paramount for achieving accurate environmental mapping and object recognition.
Data quality fundamentally impacts system reliability and decision-making accuracy. Engineers must consider numerous factors including signal-to-noise ratios, temporal resolution, and sampling fidelity. Regular calibration procedures and preventive maintenance schedules ensure sustained data integrity throughout system operation.
Data Processing and Feature Extraction
Initial sensor outputs typically require significant refinement before becoming actionable information. Sophisticated processing pipelines employ noise suppression, signal enhancement, and pattern isolation techniques to transform raw inputs into structured datasets. Effective feature identification enables systems to concentrate computational resources on operationally relevant environmental aspects.
Processing algorithm selection critically influences overall system effectiveness. Different mathematical approaches exhibit varying computational efficiencies and scenario-specific strengths. Implementation teams must balance processing demands against available hardware resources while maintaining required performance standards.
Applications Across Diverse Industries
Perception technologies enable transformative solutions across multiple sectors. Self-driving vehicles utilize these systems for real-time navigation and hazard detection. Medical fields employ similar principles for diagnostic imaging and surgical assistance. Industrial applications include precision manufacturing and automated quality assurance. Continuous technological advancements steadily expand potential implementation scenarios across virtually all industries.
The proliferation of intelligent perception systems continues to reshape human-machine interactions. These innovations drive efficiency improvements and enable previously impossible applications. Future development trajectories suggest even more profound impacts across global industries.
Challenges and Future Directions
Despite significant progress, perception systems still face substantial technical hurdles. Complex operating environments, imperfect data streams, and unpredictable conditions all present ongoing challenges. Overcoming these obstacles represents a critical requirement for achieving truly reliable autonomous systems.
Continued research focuses on enhancing system accuracy, resilience, and operational efficiency. Emerging sensor technologies, advanced processing architectures, and machine learning innovations all contribute to steady improvements. These technological advancements will ultimately determine the scope and scale of future perception system applications.
Vulnerabilities in Autonomous Driving Perception Systems
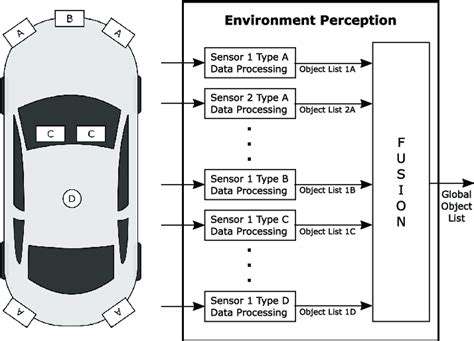
Sensor Fusion Vulnerabilities
Modern autonomous vehicles integrate multiple sensor inputs through sophisticated fusion algorithms. Imperfect synchronization between different sensor modalities can create dangerous perception gaps. Attackers could potentially exploit these vulnerabilities by introducing carefully crafted interference patterns, leading to catastrophic system misinterpretations. Comprehensive calibration protocols and exhaustive testing regimens provide essential safeguards against such threats.
Processing algorithm vulnerabilities present additional security concerns. Sophisticated cyberattacks might target specific algorithmic weaknesses to induce erroneous environmental interpretations. Potential attack vectors include manipulated sensor streams that could trigger dangerous vehicle responses. Implementing robust input validation and secure computational architectures helps mitigate these risks.
Deep Learning Model Attacks
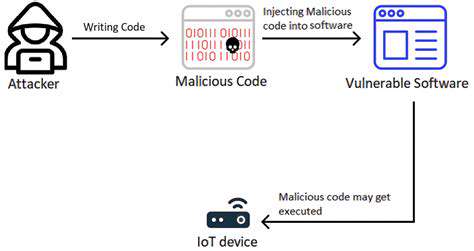
Neural network-based perception systems introduce unique security challenges. Adversarial examples—carefully modified inputs designed to deceive machine learning models—represent a particularly insidious threat. These manipulated inputs often appear legitimate to human observers while causing catastrophic model failures. Remote deployment of such attacks could lead to severe traffic incidents through object misclassification.
Training data integrity presents another critical vulnerability. Biased or contaminated training sets can produce models with dangerous blind spots or predictable failure modes. Malicious actors might intentionally introduce such biases during model development, potentially creating vehicles with exploitable weaknesses.
Data Integrity and Tampering
Maintaining uncompromised data streams proves essential for safe operation. Potential attack methods include man-in-the-middle data manipulation and false sensor signal injection. These techniques could cause systematic environmental misinterpretation with potentially fatal consequences. Cryptographic verification methods and secure data transmission protocols provide necessary protections against such threats.
Communication Channel Vulnerabilities
Inter-component communication networks represent another potential attack surface. Sophisticated attackers might intercept and modify data packets traveling between system components. Such compromised communications could lead to dangerous discrepancies between actual conditions and system perceptions. Implementing military-grade encryption and continuous channel monitoring helps maintain communication integrity.
Hardware Vulnerabilities
Physical components remain susceptible to direct tampering or sophisticated electromagnetic attacks. Malicious modification of sensor hardware could produce systematically distorted environmental data. Advanced protection measures include tamper-proof hardware designs, secure manufacturing processes, and comprehensive physical security protocols.
Cybersecurity Protocols and Countermeasures
Comprehensive security frameworks must address all potential attack vectors. Essential protections include end-to-end encryption, anomaly detection systems, and regular penetration testing. Continuous behavioral monitoring enables early detection of potential compromises. Timely software updates and vulnerability patching remain critical for maintaining long-term system security.
Ethical Considerations in Autonomous Driving Perception
Security vulnerabilities raise profound ethical questions regarding autonomous vehicle deployment. Potential safety failures necessitate clear liability frameworks and fail-safe mechanisms. Transparent system designs and robust ethical guidelines must guide technological development to ensure public safety and maintain societal trust. Comprehensive risk assessment protocols should inform all stages of system development and deployment.