What is Autonomous Emergency Steering (AES)?
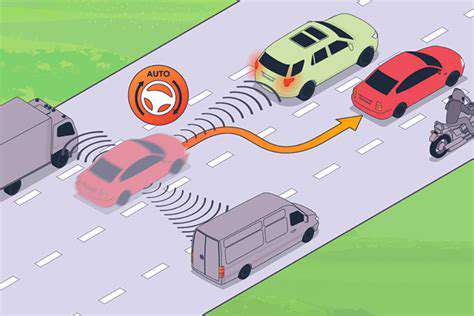
Autonomous Emergency Steering Explained
Modern vehicles increasingly incorporate autonomous emergency steering (AES), a vital safety mechanism that takes control of steering to prevent collisions. Unlike passive safety features, AES actively intervenes by processing real-time data from multiple sensors to identify imminent dangers. This proactive approach sets it apart from traditional safety systems, as it doesn't just warn drivers but physically assists in avoiding accidents.
Road safety experts emphasize that AES represents a paradigm shift in vehicular protection. By anticipating collisions before they occur, this technology significantly reduces accident rates in challenging driving scenarios where human reaction times might prove insufficient.
Key Components of AES Systems
The effectiveness of AES relies on an intricate network of components working in perfect synchronization. High-resolution cameras, LiDAR sensors, and radar systems form the eyes of the system, continuously scanning the vehicle's surroundings with remarkable precision. These sensors feed data to powerful onboard computers running sophisticated collision-avoidance algorithms.
What makes these systems particularly remarkable is their processing speed. The onboard computers can analyze complex traffic situations and calculate optimal avoidance maneuvers in milliseconds - faster than any human driver could react. This rapid processing is what enables AES to prevent accidents in split-second emergency situations.
How AES Systems Detect Hazards
Hazard detection in AES systems involves a multi-layered approach to environmental perception. Cameras provide visual recognition of objects, while radar detects their speed and distance. The fusion of these data streams creates a comprehensive 360-degree awareness bubble around the vehicle, allowing the system to track multiple potential threats simultaneously.
Advanced machine learning algorithms process this sensory input to distinguish between false positives and genuine collision risks. The system can differentiate between a plastic bag blowing across the road and a child running into the street, ensuring appropriate responses to actual dangers while minimizing unnecessary interventions.
AES Systems and Driver Assistance
It's crucial to understand that AES serves as a co-pilot rather than a replacement for human drivers. The system activates only when it detects an imminent collision that the driver hasn't responded to, providing that critical last-resort intervention. This collaborative approach maintains driver control while adding an important safety net for moments of distraction or unexpected hazards.
AES and Pedestrian Detection
Pedestrian protection represents one of AES's most valuable capabilities. Modern systems can identify vulnerable road users even in challenging conditions like low light or crowded urban environments. The algorithms can predict pedestrian trajectories with surprising accuracy, calculating whether an evasive steering maneuver could prevent an accident while maintaining vehicle stability.
This capability becomes particularly important in urban environments where pedestrians might suddenly step into the road from between parked cars or at poorly marked crossings. AES systems can detect these unpredictable movements and initiate avoidance maneuvers more reliably than human drivers in many cases.
AES and Vehicle-to-Everything (V2X) Communication
The next evolution of AES technology involves integration with V2X networks. This allows vehicles to receive real-time data about hazards beyond the range of their onboard sensors - such as an accident around a blind corner or a pedestrian crossing several cars ahead. V2X essentially gives AES systems second sight, dramatically expanding their preventive capabilities.
Early trials have shown that V2X-enhanced AES can prevent accidents caused by limited visibility, especially in complex urban environments or during adverse weather conditions where sensors might be compromised.
The Future of Autonomous Emergency Steering
As technology progresses, we're seeing AES evolve from a collision avoidance system to a comprehensive safety platform. Future iterations may incorporate predictive analytics to anticipate potential hazards before they fully develop. Researchers are particularly excited about AI systems that can learn from millions of driving scenarios, developing increasingly sophisticated response patterns to unusual situations.
Another promising development involves integrating AES with other vehicle systems like stability control and adaptive suspension, allowing for more aggressive but controlled avoidance maneuvers while maintaining passenger comfort and vehicle stability.
How Does AES Work?
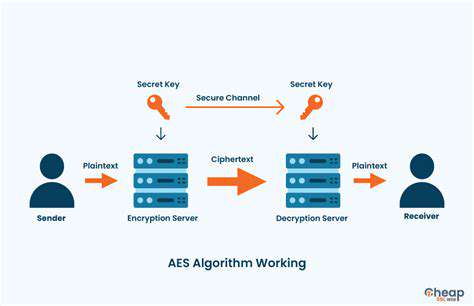
Understanding the Fundamentals of AES
The Advanced Encryption Standard operates on a remarkably elegant yet complex mathematical foundation. Rather than working with data as a continuous stream, AES processes information in discrete 128-bit blocks, applying multiple transformation rounds to each block. This block cipher approach allows for both security and computational efficiency, making it practical for everything from financial transactions to secure communications.
What makes AES particularly robust is its use of substitution-permutation network principles. Each transformation round applies multiple operations that substitute and rearrange data in ways that make patterns extremely difficult to discern without the proper key. This layered approach creates what cryptographers call confusion and diffusion - scrambling both the relationship between the key and ciphertext, and the statistical structure of the plaintext.
The Key Scheduling Algorithm
The key expansion process in AES is a masterpiece of cryptographic engineering. Starting with the original secret key (typically 128, 192, or 256 bits), the algorithm generates a key schedule - essentially a series of round keys for each encryption stage. This expansion isn't simply copying bits; it involves sophisticated transformations that ensure each round key bears no obvious relationship to its predecessors while maintaining cryptographic strength.
Interestingly, the key schedule incorporates non-linear transformations that prevent attackers from working backward from partial key information. Even if an attacker knew several round keys, deducing the original master key would remain computationally infeasible due to these carefully designed transformations.
The Encryption Rounds
Each encryption round in AES performs four distinct operations on the data block. The SubBytes step replaces each byte with another according to a predefined substitution table (S-box). ShiftRows rearranges bytes within the block, while MixColumns performs matrix multiplication to diffuse bits across columns. Finally, AddRoundKey combines the block with the round key, completing the transformation.
The beauty of this structure lies in how each operation complements the others. While SubBytes provides non-linearity, ShiftRows and MixColumns ensure thorough diffusion of bits across the entire block. The AddRoundKey step then ties everything to the specific encryption key, making each encryption unique.
Substitution-Permutation Network (SPN)
The SPN structure represents the cryptographic heart of AES. Unlike older cipher designs that relied on complex mathematical operations, AES's SPN approach achieves security through carefully orchestrated simplicity. The combination of substitution (via S-boxes) and permutation (through ShiftRows and MixColumns) creates an avalanche effect where changing a single bit in the plaintext affects nearly all bits in the ciphertext.
This structure has proven remarkably resistant to cryptanalysis. Even after decades of study, no practical weaknesses have been found in AES's SPN design when used with proper key sizes and implementation practices.
The Initial Round
AES begins with a unique preliminary step that often surprises those new to cryptographic algorithms. Before any transformations occur, the algorithm performs an initial AddRoundKey operation. This simple but crucial step immediately obscures the plaintext by XORing it with the first round key, ensuring that all subsequent operations work on already-encrypted data.
This initial key addition serves an important security purpose. Without it, the first round's SubBytes operation would work directly on the plaintext, potentially revealing patterns that could aid cryptanalysis. By first mixing in key material, AES ensures all transformations work on key-dependent data from the very beginning.
The Final Round
The last round of AES features a subtle but intentional deviation from the standard round structure. By omitting the MixColumns step, the final round creates a more efficient inverse operation for decryption while maintaining security. This optimization demonstrates the algorithm's elegant design - achieving maximum security with minimal computational overhead.
Interestingly, this modification doesn't weaken the cipher because the final AddRoundKey provides sufficient diffusion when combined with the previous rounds' transformations. This careful balancing of security and performance is characteristic of AES's thoughtful design.
Decryption Process
Decryption in AES mirrors the encryption process but applies inverse transformations in reverse order. The elegant symmetry of the algorithm allows for efficient implementation of both encryption and decryption using largely the same circuitry or code structure. Each decryption round essentially unwinds the transformations applied during encryption.
What's particularly noteworthy is how the inverse operations maintain the algorithm's security properties. The inverse S-boxes and reverse ShiftRows perfectly counteract their encryption counterparts, while the identical AddRoundKey operation (using the same round keys) completes the reversal. This mathematical harmony ensures that decryption reliably recovers the original plaintext when the correct key is used.